Hardwear.io NL 2023 | Dissecting The Modern Android Data Encryption Scheme - Maxime Bellom & Damiano - YouTube
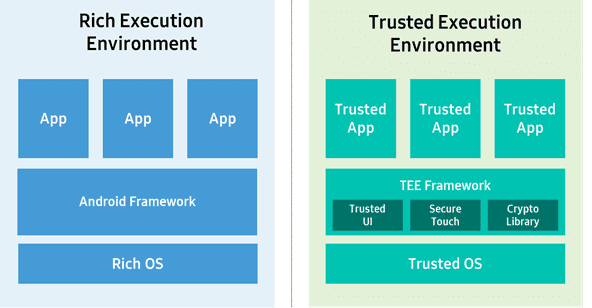
How to use the Android Keystore to store passwords and other sensitive information - Android Authority

SEBASTiAn: A static and extensible black-box application security testing tool for iOS and Android applications - SoftwareX

Can multiple Android Applications(same device) share same key-pair for Passwordless Authentication using FIDO 2 Protocol? - Stack Overflow

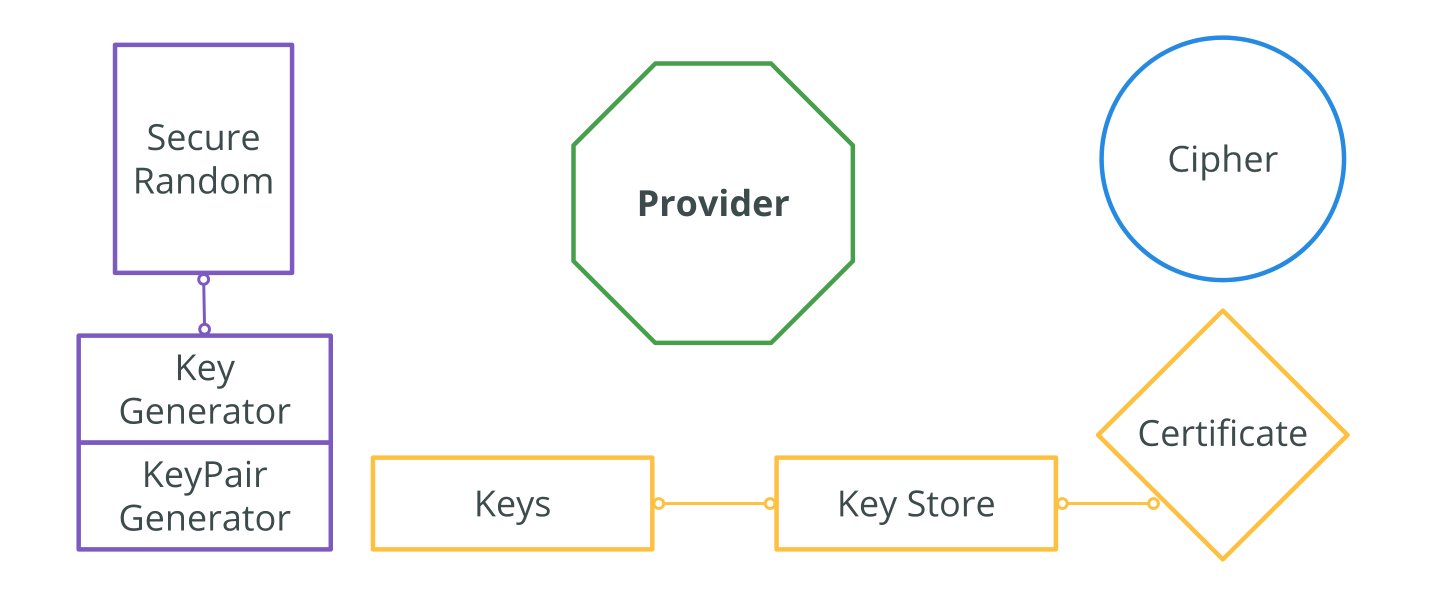
Using the Android Keystore system to store and retrieve sensitive information | by Josias Sena | Medium
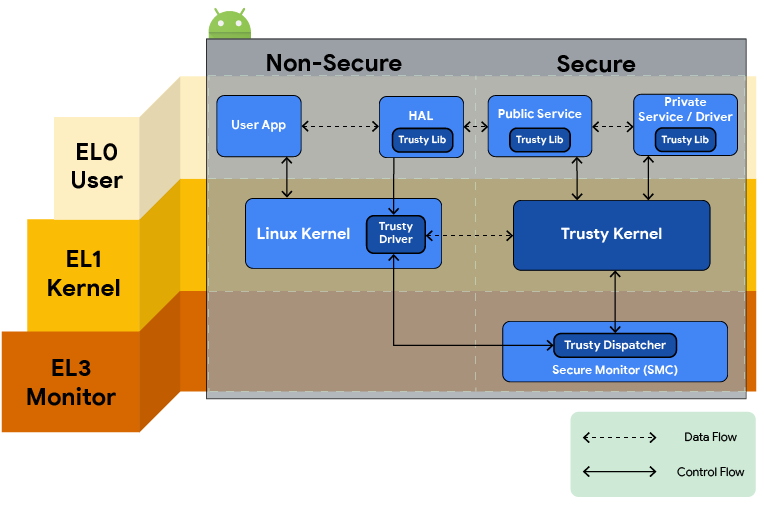
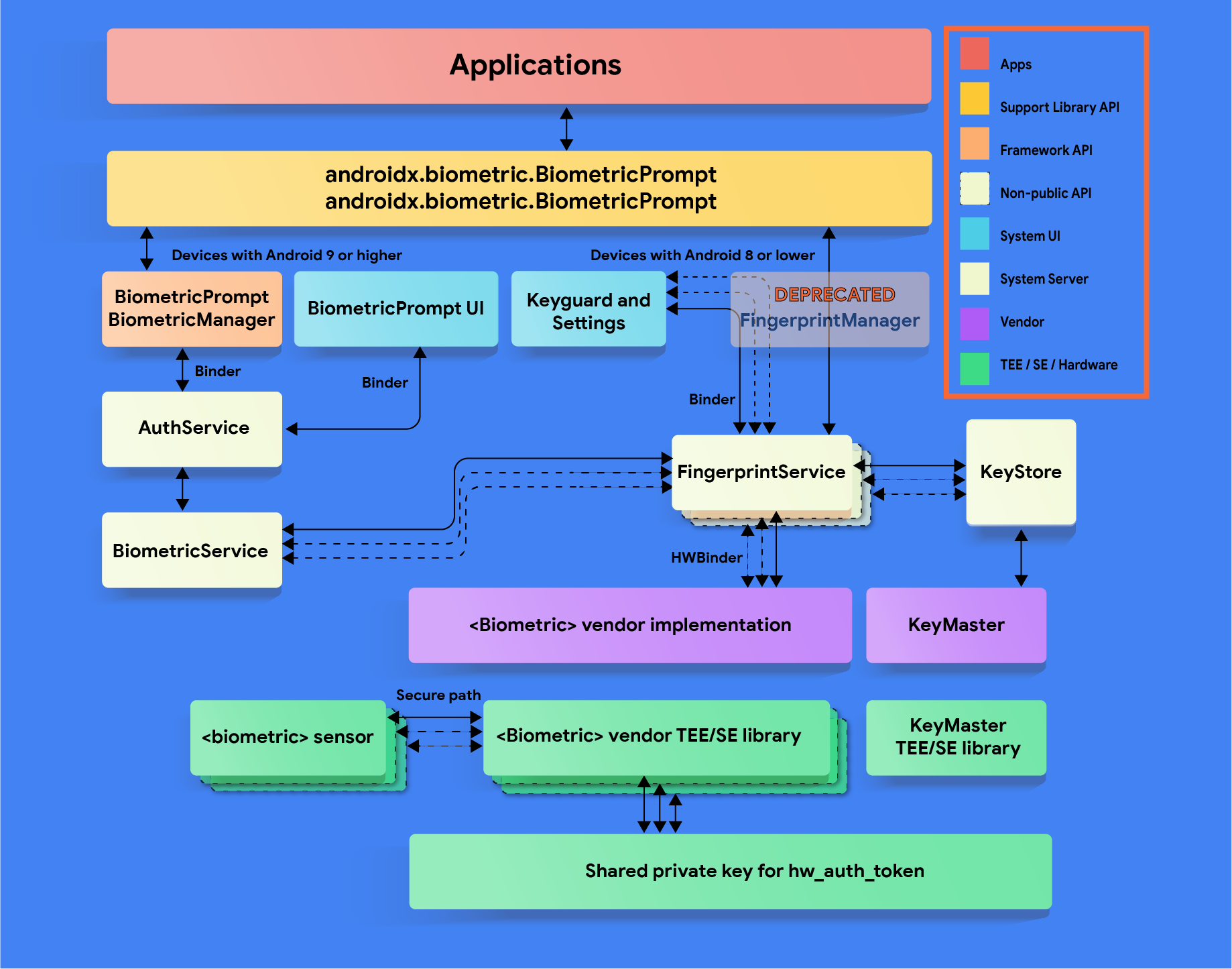
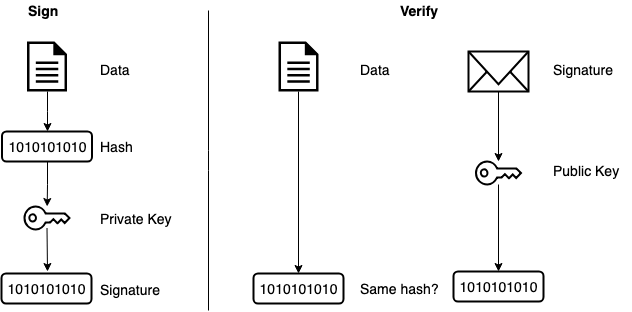
Cryptographic Key Handling in Android: from software to StrongBox and everything in between | by Dario Incalza | ProAndroidDev