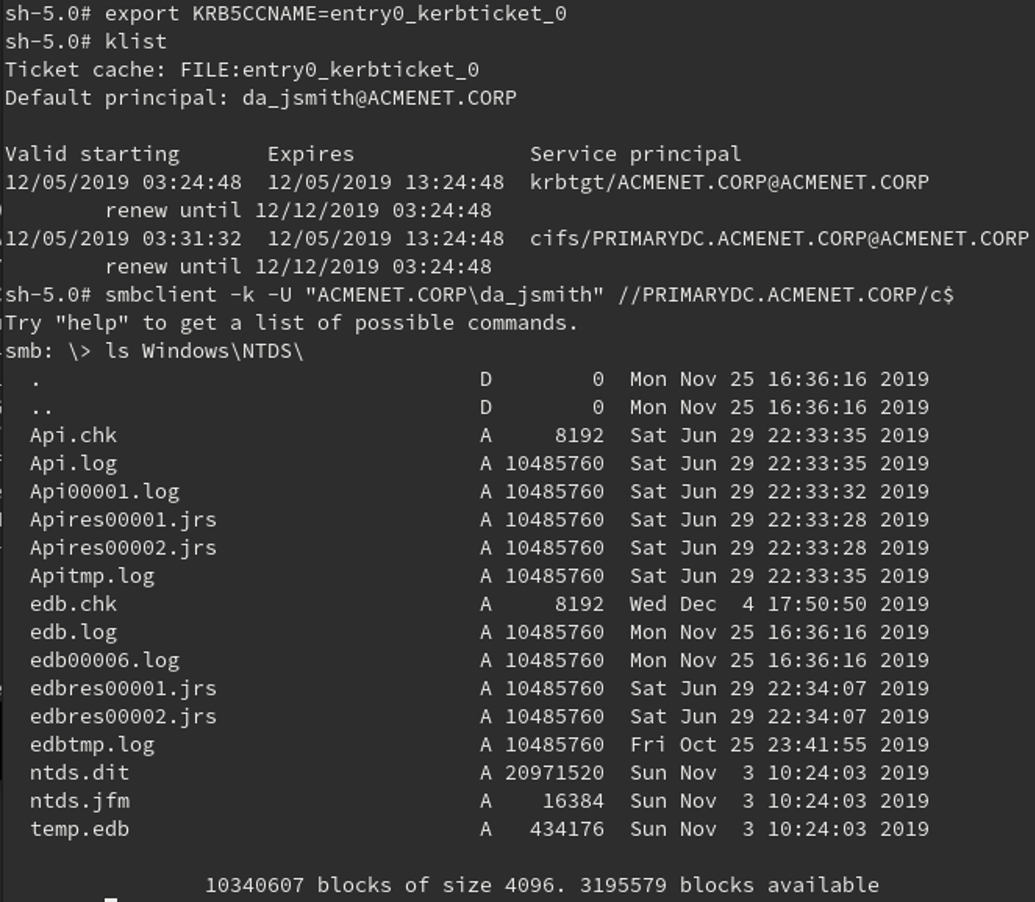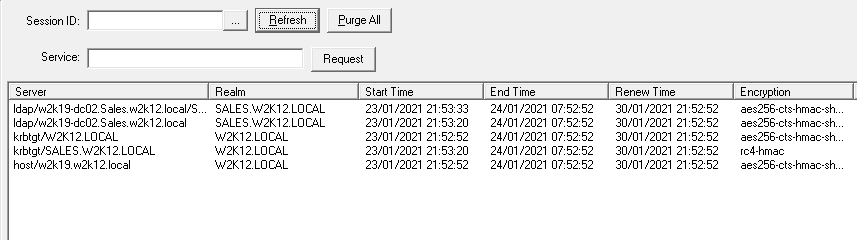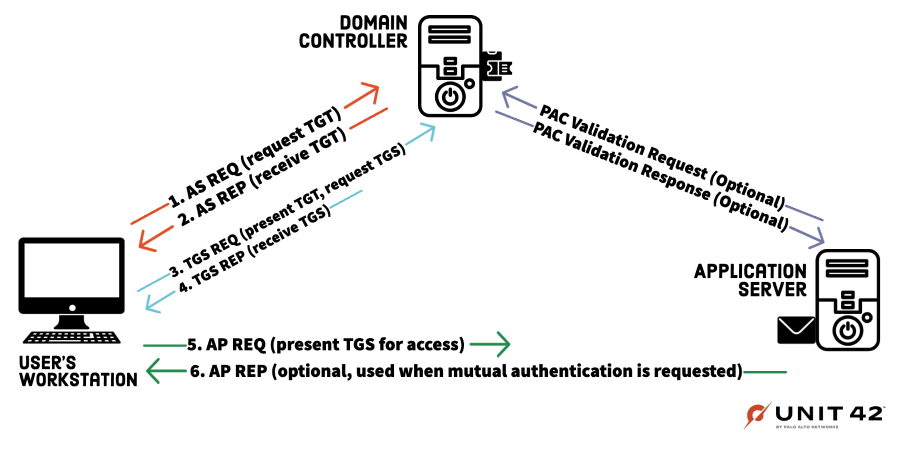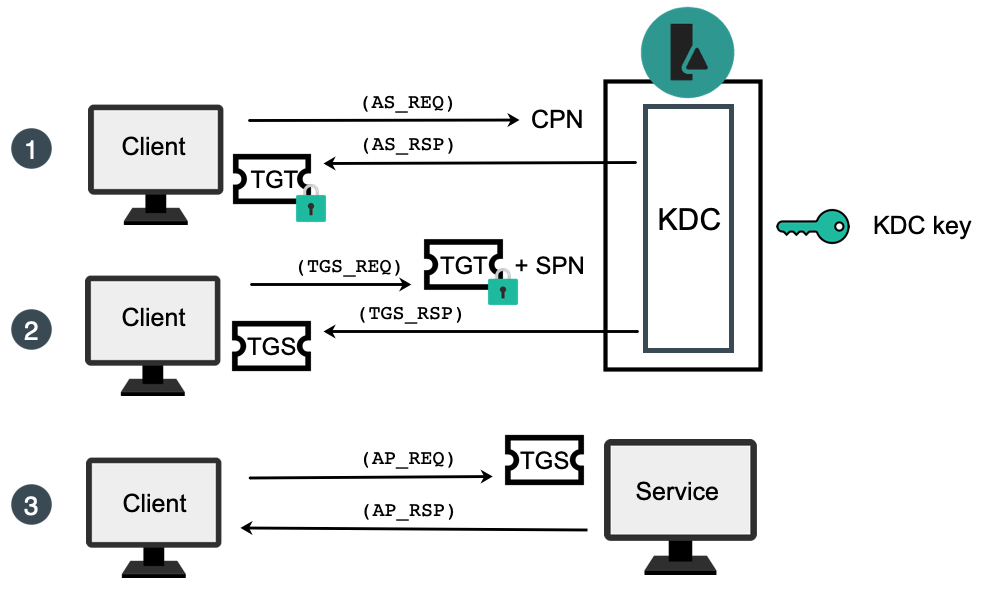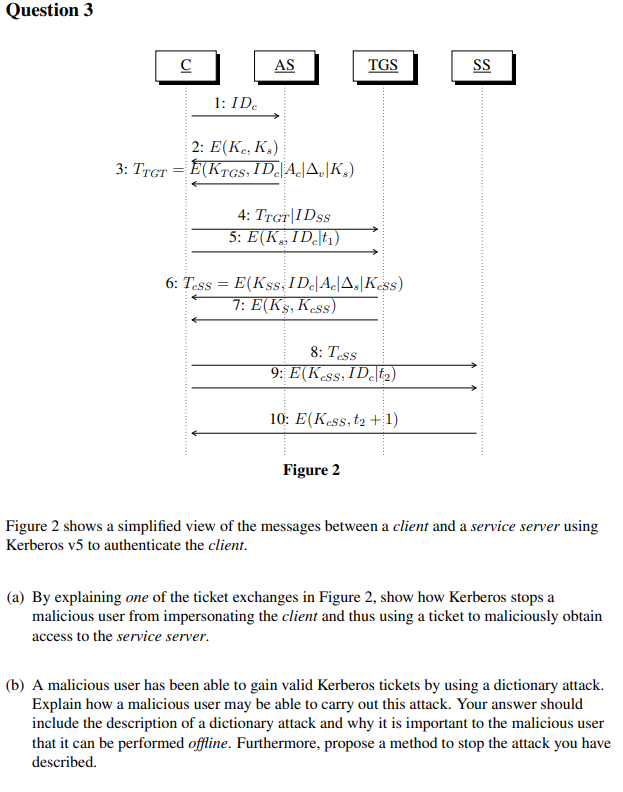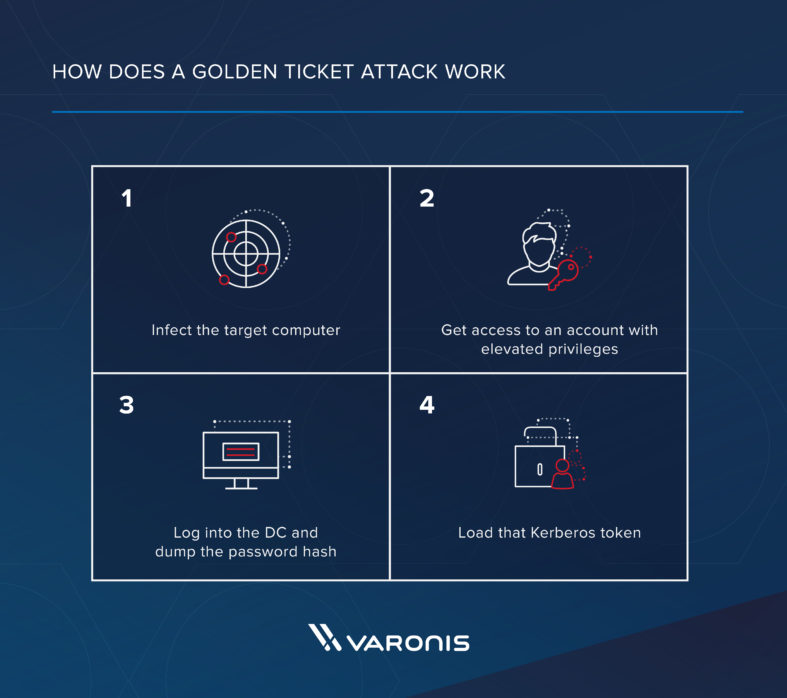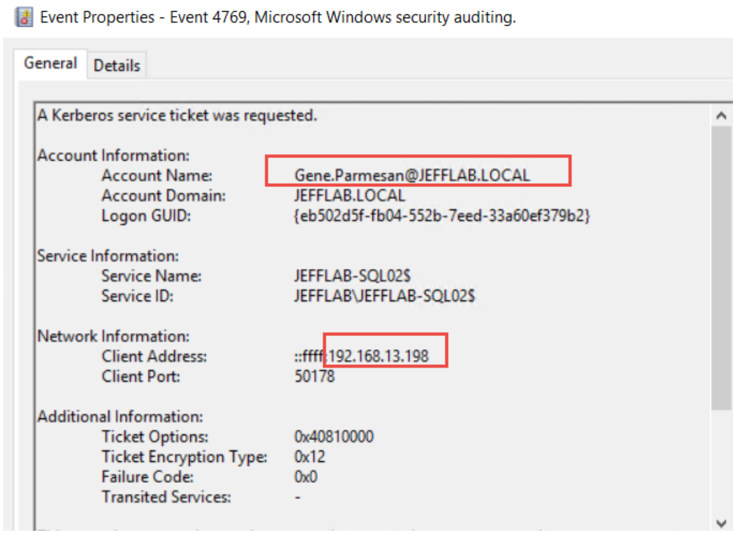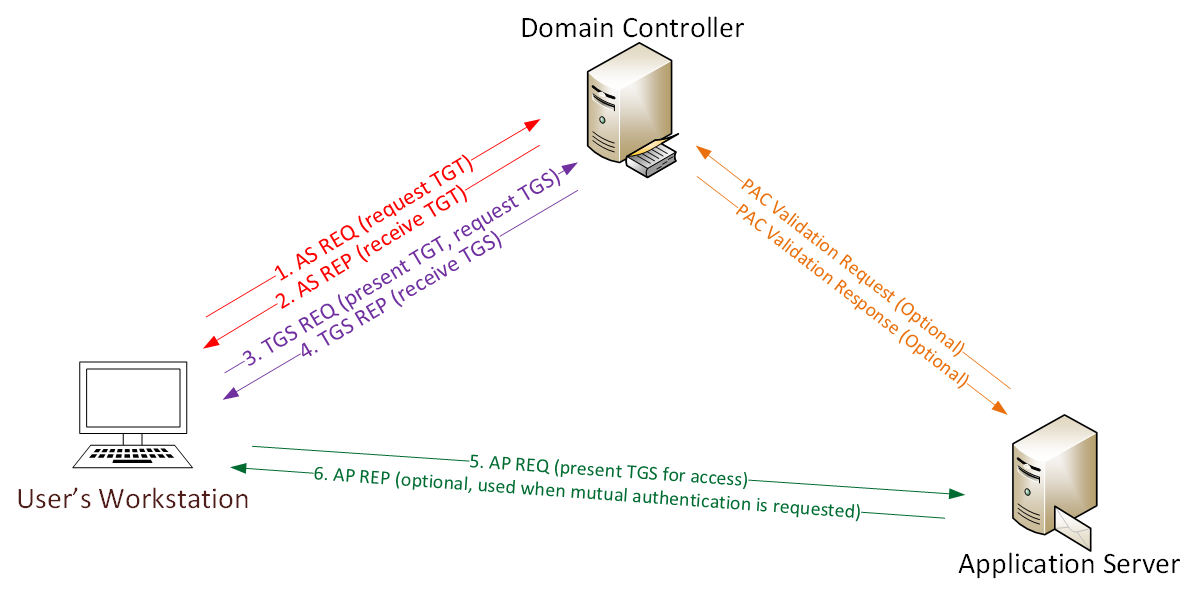
It's All About Trust – Forging Kerberos Trust Tickets to Spoof Access across Active Directory Trusts » Active Directory Security
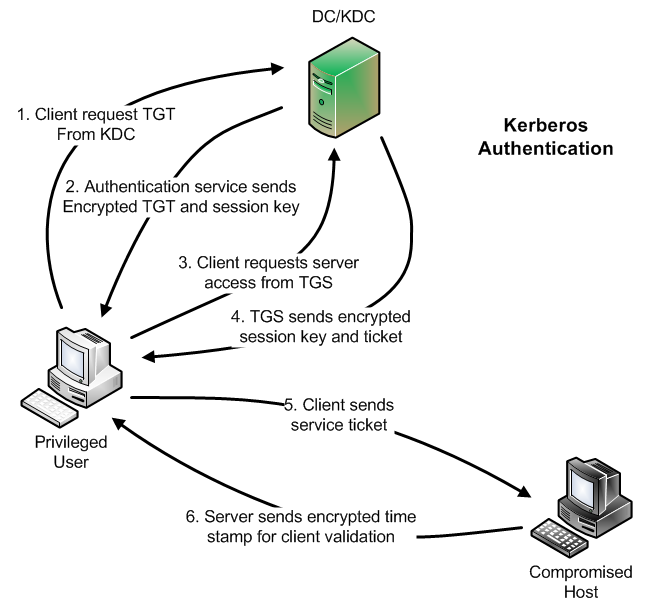
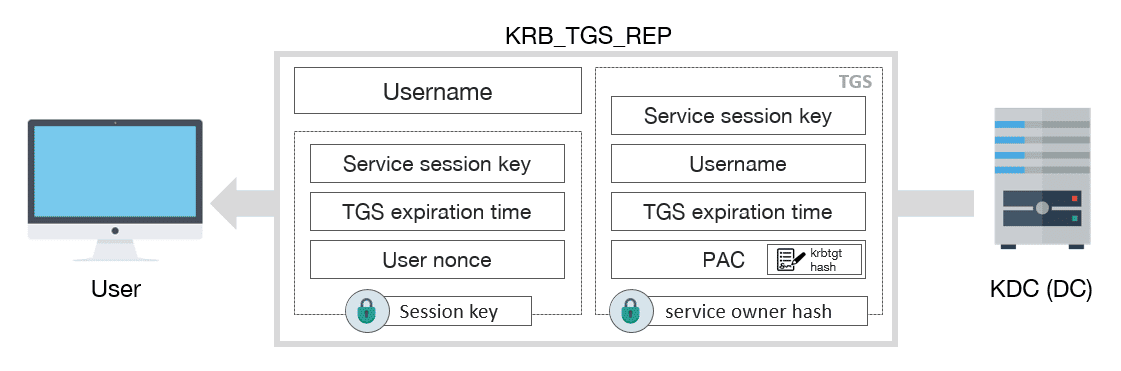
SANS Digital Forensics and Incident Response Blog | Kerberos in the Crosshairs: Golden Tickets, Silver Tickets, MITM, and More | SANS Institute
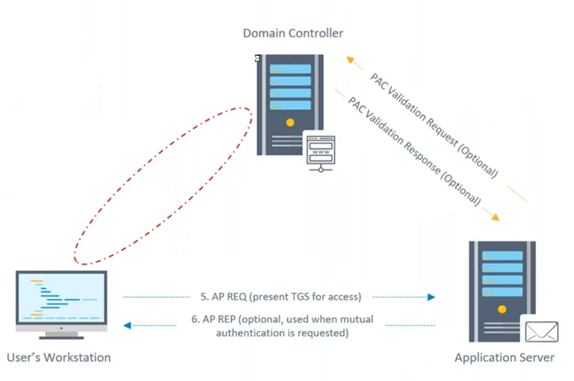
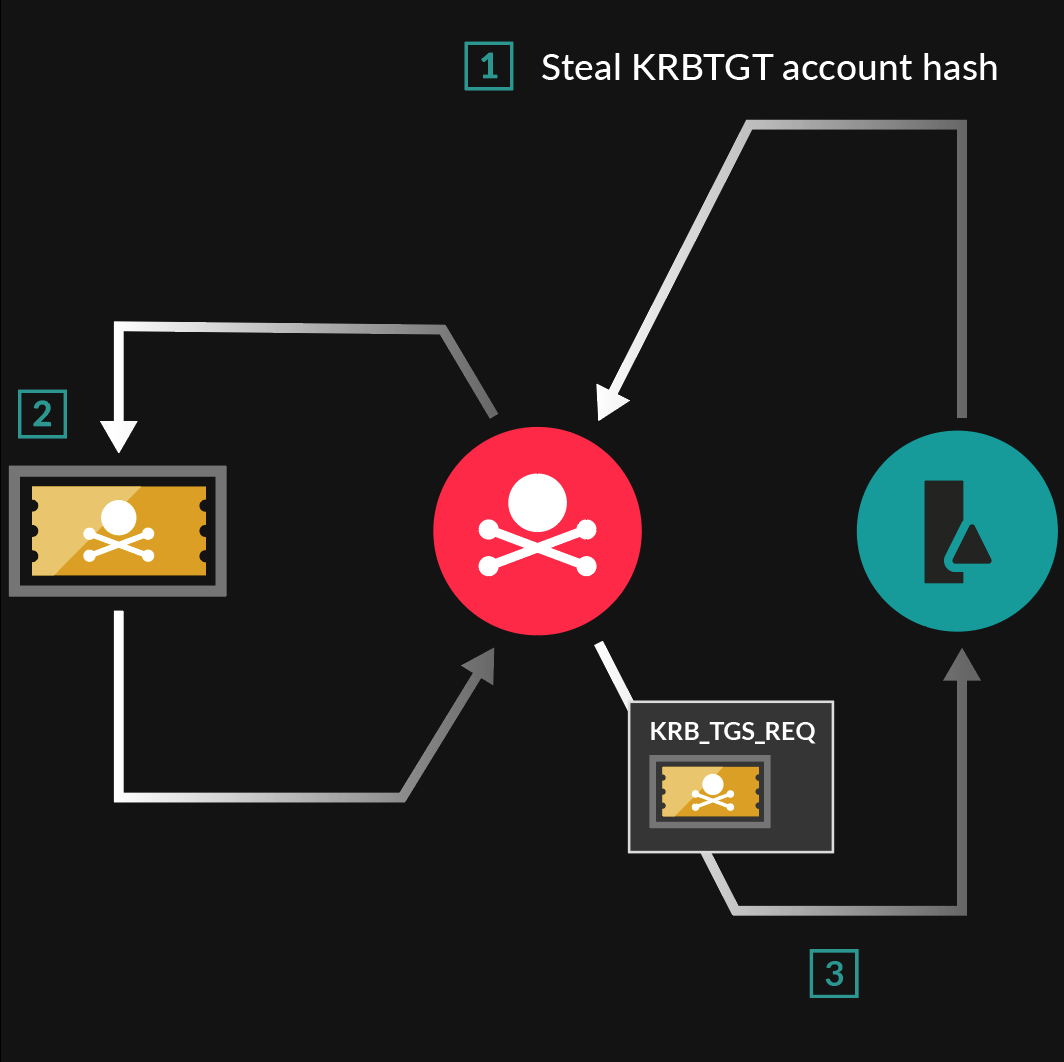
Getting Inside the Mind of an Attacker: After the Breach - Achieving Persistence with Golden and Silver Tickets | Core Security Blog
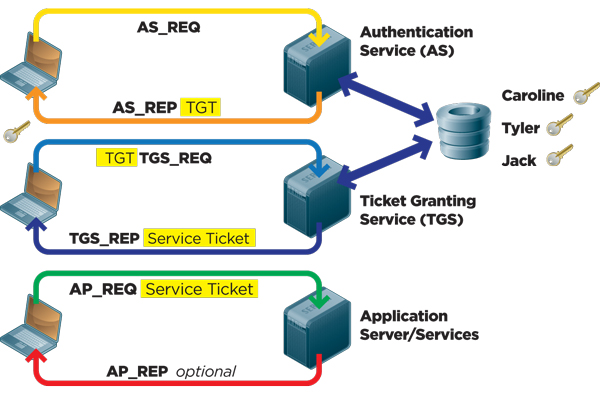
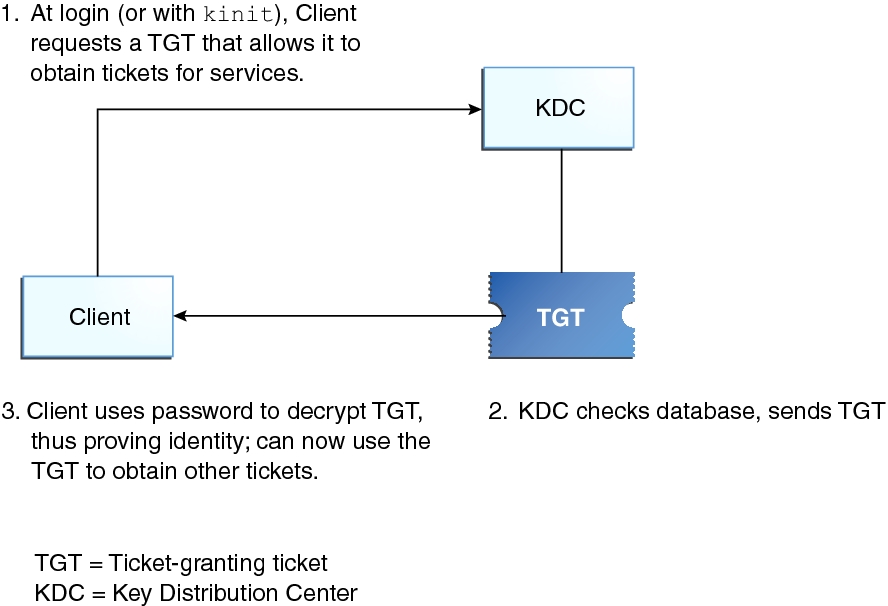
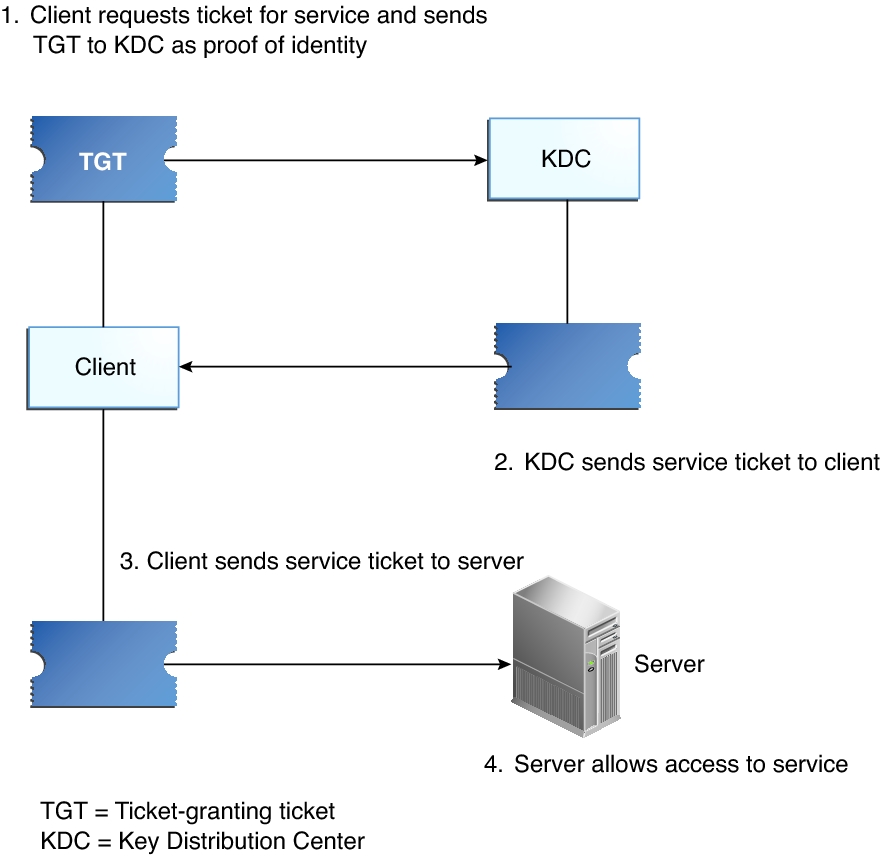
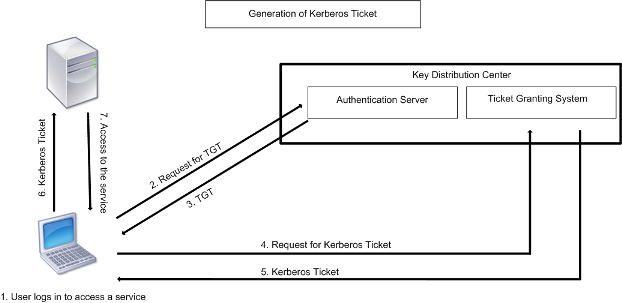
Kerberos Authentication 101: Understanding the Essentials of the Kerberos Security Protocol -- Redmondmag.com
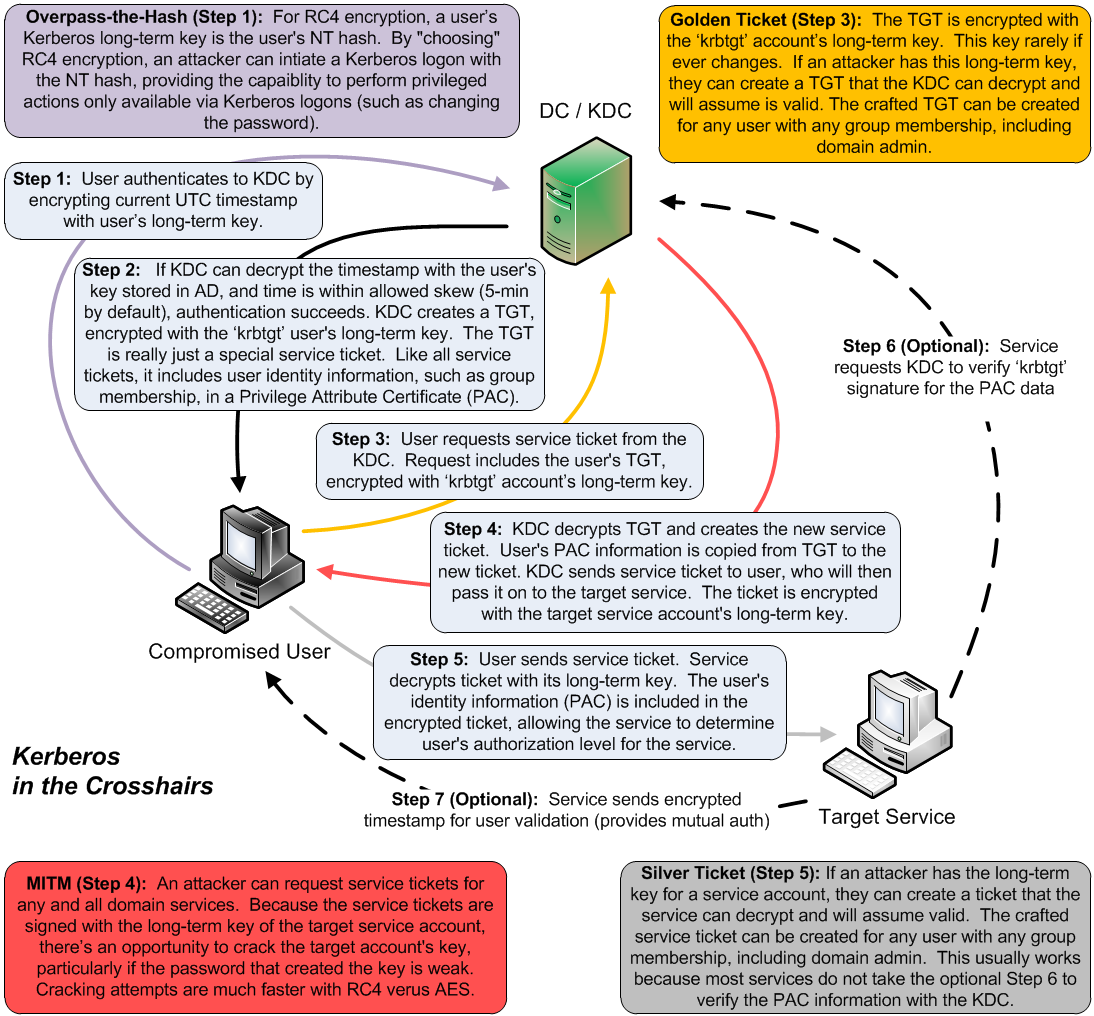
SANS Digital Forensics and Incident Response Blog | Kerberos in the Crosshairs: Golden Tickets, Silver Tickets, MITM, and More | SANS Institute